来源:自学PHP网 时间:2015-04-17 13:03 作者: 阅读:次
[导读] 简要描述:android平台使用sqlite做为数据库,对于数据库查询,如果开发者采用字符串连接方式构造SQL语句,就会产生sql注入。详细说明:android自身实现了一个sqlite操作类SQLiteOpenHelper,...
|
简要描述:
android平台使用sqlite做为数据库,对于数据库查询,如果开发者采用字符串连接方式构造SQL语句,就会产生sql注入。 详细说明: android自身实现了一个sqlite操作类SQLiteOpenHelper,我们继承此类,然后重载onCreate,onUpgrade等方法 DatabaseHelper.java如下: package com.xiaod.sqlinj; import android.content.Context; import android.database.sqlite.SQLiteDatabase; import android.database.sqlite.SQLiteDatabase.CursorFactory; import android.database.sqlite.SQLiteOpenHelper; public class DatabaseHelper extends SQLiteOpenHelper { public static final String TB_NAME="usertable"; public static final String ID="_id"; public static final String USERNAME="username"; public static final String PASSWORD="password"; DatabaseHelper(Context context, String name, CursorFactory cursorFactory, int version) { super(context, name, cursorFactory, version); } @Override public void onCreate(SQLiteDatabase db) { db.execSQL("CREATE TABLE IF NOT EXISTS "+ TB_NAME+" ("+ID+" INTEGER PRIMARY KEY,"+ USERNAME+" VARCHAR,"+PASSWORD+" VARCHAR )"); db.execSQL("INSERT INTO "+TB_NAME+"("+USERNAME+","+PASSWORD+") VALUES"+"('admin','admin888')"); db.execSQL("INSERT INTO "+TB_NAME+"("+USERNAME+","+PASSWORD+") VALUES"+"('root','root123')"); db.execSQL("INSERT INTO "+TB_NAME+"("+USERNAME+","+PASSWORD+") VALUES"+"('xiaod','xiaodwin')"); } @Override public void onUpgrade(SQLiteDatabase db, int oldVersion, int newVersion) { } @Override public void onOpen(SQLiteDatabase db) { super.onOpen(db); } } 界面上添加一个查询框,查询按钮,在textview显示查询结果 SqlinjActivity.java如下: package com.xiaod.sqlinj; import android.app.Activity; import android.database.Cursor; import android.database.sqlite.SQLiteDatabase; import android.os.Bundle; import android.view.View; import android.view.View.OnClickListener; import android.widget.Button; import android.widget.EditText; import android.widget.TextView; public class SqlinjActivity extends Activity { public static final String DB_NAME = "sqlinj.db"; public static final int VERSION = 1; private String result = ""; private TextView m_tv; private EditText m_et; DatabaseHelper m_dbhelper; SQLiteDatabase m_db; Button m_btnselect; /** Called when the activity is first created. */ @Override public void onCreate(Bundle savedInstanceState) { super.onCreate(savedInstanceState); setContentView(R.layout.main); m_tv = (TextView)findViewById(R.id.tv_view); m_btnselect = (Button)findViewById(R.id.btn_select); m_et = (EditText)findViewById(R.id.et_id); m_btnselect.setOnClickListener(new OnClickListener(){ @Override public void onClick(View arg0) { // TODO Auto-generated method stub String m_id = m_et.getText().toString(); m_tv.setText(ShowData(m_id)); } }); m_dbhelper = new DatabaseHelper(this, DB_NAME, null, VERSION); m_db = m_dbhelper.getWritableDatabase(); } private String ShowData(String m_id) { result = ""; Cursor m_cursor; String m_argv[] = {m_id}; m_cursor = m_db.rawQuery("SELECT * FROM usertable WHERE _id = '" + m_id +"'", null); m_cursor.moveToFirst(); while(!m_cursor.isAfterLast()){ result += "id: " + m_cursor.getInt(0) + "\n" + "user: " + m_cursor.getString(1) + "\n" + "pass: " + m_cursor.getString(2) + "\n\n"; m_cursor.moveToNext(); } m_cursor.close(); return result; } } 漏洞证明: 在ShowData函数中,通过传递id号,来查询记录,而54行语句SELECT * FROM usertable WHERE _id= 使用字符串连接方式,构造SQL语句。我们运行程序,测试下是否能注入。 运行后,提交1,返回正常 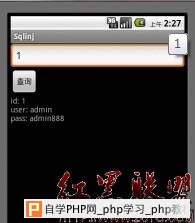 提交2′and ’1′=’1返回正常 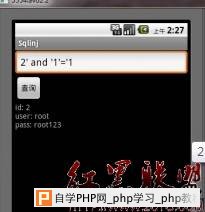 提交2′and ’1′=’2查询不到数据 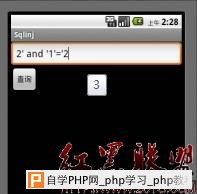 输入2′or _id <> ‘ 返回所有数据 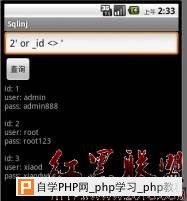 修复方案: sql injection防护方式和常规思路一致,使用参数化查询 增加一个数组存储查询参数 作者:冷森@乌云 |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com