来源:自学PHP网 时间:2015-04-17 13:03 作者: 阅读:次
[导读] CVE-2011-4107 PoC - phpMyAdmin Local File Inclusion via XXE injectionAn interesting local file inclusion vulnerability has been recently published. An XXE (XML eXternal Enti......
|
CVE-2011-4107 PoC - phpMyAdmin Local File Inclusion via XXE injection An interesting local file inclusion vulnerability has been recently published. An XXE (XML eXternal Entity) injection attack, which affects phpMyAdmin 3.4.x previous to 3.4.7.1 and 3.3.x previous to 3.3.10.5. - CVE-2011-4107 The issue is located in the libraries\import\xml.php file, where the simplexml_load_string() function is called without validating the existence of a reference to an external entity on the file:
Patched versions make use of the libxml_disable_entity_loader() PHP function before loading the XML document, in order to prevent the injection. libxml_disable_entity_loader() function disables the ability to load external entities. phpMyAdmin offers the functionality of importing a database from a user-specified XML file. In vulnerable versions importing a specially-crafted XML file which contains an external XML entity permits an authenticated attacker to retrieve a local file from the server or network (limited by the privileges of the user running the web server). It is well understood that the LOAD_FILE MySQL function could be used to gain read access to files in the database file system, however there are configurations where phpMyAdmin is installed on a different host than the database and therefore exploitation of this issue could become handy in penetration testing engagements. SECFORCE has developed a metasploit module to assist the exploitation of this vulnerability. It is available for download from our security tools section on our website. This module automates the process of local file inclusion in the following way:
The module has the options shown in the following screenshot:
An example of a successful run of the module is presented in the screenshot below: 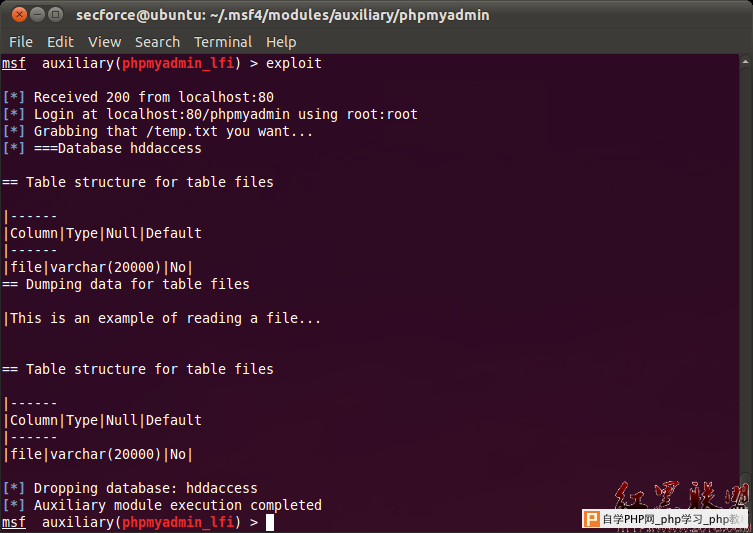 Defining XML external entity (XXE) injection attack as part of XML injection vulnerability: XML injection XML Injection is when is is possible to change the values of an XML document and the XML parser fails to make an appropriate data validation this way making the injection possible. XML external entity injection attack (XXE) “External Entity: The set of valid entities can be extended by defining new entities. If the definition of an entity is a URI, the entity is called an external entity. Unless configured to do otherwise, external entities force the XML parser to access the resource specified by the URI, e.g., a file on the local machine or on a remote systems. This behavior exposes the application to XML eXternal Entity (XXE) attacks, which can be used to perform denial of service of the local system, gain unauthorized access to files on the local machine, scan remote machines, and perform denial of service of remote systems.” - (OWASP-DV-008) XXE Example: <?xml version="1.0" encoding="ISO-8859-1"?> <!DOCTYPE foo [ <!ELEMENT foo ANY > <!ENTITY xxe SYSTEM "file:///c:/boot.ini" >]><foo>&xxe;</foo> phpMyAdmin has released patched versions available for download from here. |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com